shadowsocks on azure containers from scratch
create a new cloud shell instance (to use azure cli)
https://portal.azure.com/#cloudshell/
create azure resource group if not present
az group create --name e6lsocks --location eastus
create azure container registry
az acr create --sku Basic -g e6lsocks -n e6lacr
create acr user, give owner perms
ACR_NAME=e6lacr
SERVICE_PRINCIPAL_NAME=acruser
ACR_REGISTRY_ID=$(az acr show --name $ACR_NAME --query "id" --output tsv)
PASSWORD=$(az ad sp create-for-rbac --name $SERVICE_PRINCIPAL_NAME --scopes $ACR_REGISTRY_ID --role owner --query "password" --output tsv)
USER_NAME=$(az ad sp list --display-name $SERVICE_PRINCIPAL_NAME --query "[].appId" --output tsv)
echo "Service principal ID: $USER_NAME"
echo "Service principal password: $PASSWORD"
pull and push container image (client-side, not cloud shell)
docker pull ghcr.io/akafeng/shadowsocks-rust
docker login e6lacr.azurecr.io
(login using service principal id and password)
docker tag ghcr.io/akafeng/shadowsocks-rust e6lacr.azurecr.io/shado
docker push e6lacr.azurecr.io/shado
run container
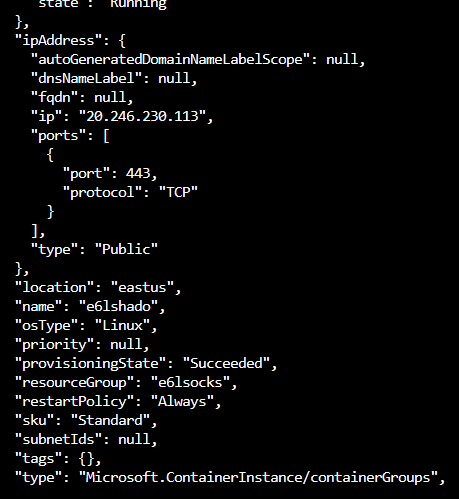
az container create -g e6lsocks --name e6lshado --image e6lacr.azurecr.io/shado --ip-address public --ports 443 --environment-variables 'SERVER_PORT'='443'
(login using service principal id and password)
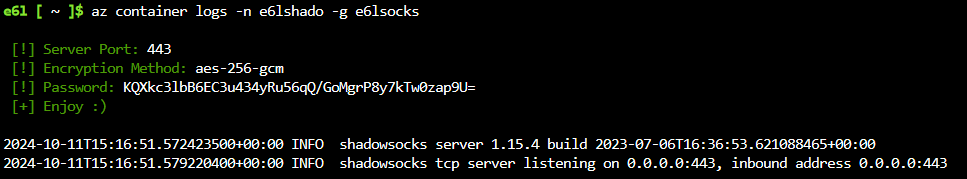
az container logs -n e6lshado -g e6lsocks
connect
connect using shadowsocks-rust, grab a copy from https://github.com/shadowsocks/shadowsocks-rust/releases.
then connect executing the following command:
sslocal.exe -s 20.246.230.113:443 -k 'KQXkc3lbB6EC3u434yRu56qQ/GoMgrP8y7kTw0zap9U=' --encrypt-method aes-256-gcm -b 127.0.0.1:1081 -v
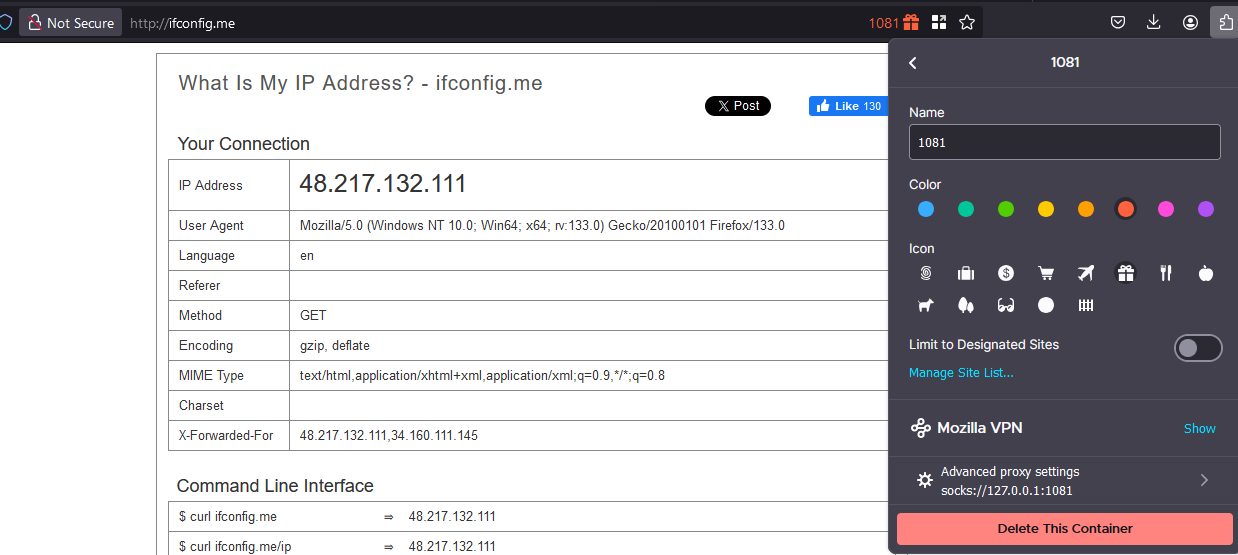
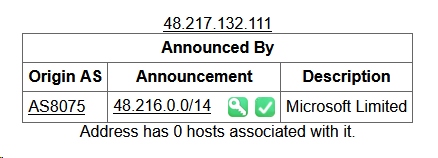
set up your new socks proxy running at localhost:1081 into a supported application (e.g firefox)