ref: https://gitlab.torproject.org/legacy/trac/-/wikis/doc/TorifyHOWTO/IsolatingProxy
note: this is a very basic/low-effort method, IP leaks can happen if wireguard gets killed on the gateway. stricter firewall rules are required on the gateway/router vm to prevent leaks (e.g allow outbound traffic only to wireguard server and deny everything else on the NAT interface).
Setup Preview
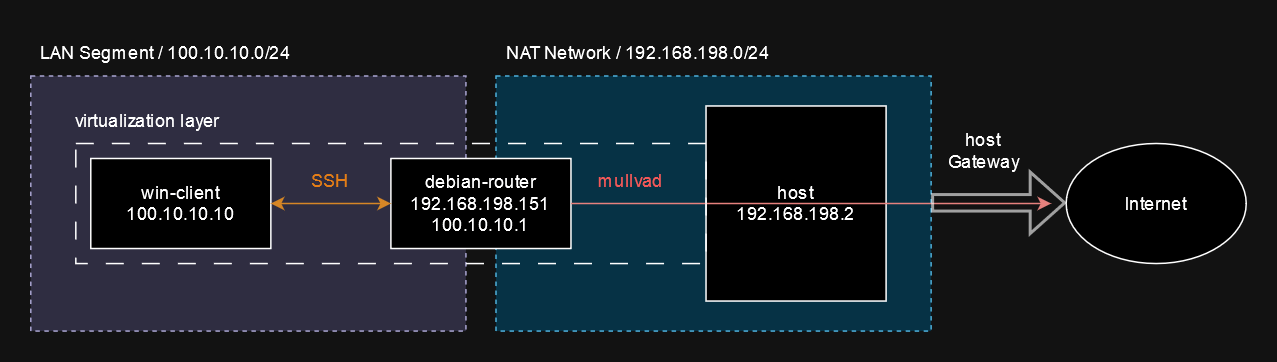
Gateway / Router
- Name: debian-router
- IP (interface 1, LAN): 100.10.10.1
- IP (interface 2, NAT): 192.168.198.151
- OS: Debian 12 Minimal
install required packages
apt install wireguard-tools resolvconf
setup networking
nano /etc/network/interfaces
allow-hotplug ens37
iface ens37 inet static
address 192.168.198.151/24
gateway 192.168.198.2 # NAT Router, provides Internet
allow-hotplug ens33
iface ens33 inet static
address 100.10.10.1/24 # "router" IP on LAN Segment
create wireguard mullvad config
nano /etc/wireguard/usa.conf
[Interface]
PrivateKey = [REDACTED]
Address = 10.[REDACTED]/32
DNS = 10.64.0.1
PostUp = iptables -I OUTPUT ! -o %i -m mark ! --mark $(wg show %i fwmark) -m addrtype ! --dst-type LOCAL -j REJECT && ip6tables -I OUTPUT ! -o %i -m mark ! --mark $(wg show %i fwmark) -m addrtype ! --dst-type LOCAL -j REJECT
PreDown = iptables -D OUTPUT ! -o %i -m mark ! --mark $(wg show %i fwmark) -m addrtype ! --dst-type LOCAL -j REJECT && ip6tables -D OUTPUT ! -o %i -m mark ! --mark $(wg show %i fwmark) -m addrtype ! --dst-type LOCAL -j REJECT
[Peer]
PublicKey = wcmmadJObux2/62ES+QbIO21BkU7p2I0s6n4WNZZgW0=
AllowedIPs = 0.0.0.0/0
Endpoint = 149.40.50.112:443
postup+predown scripts extracted from https://mullvad.net/en/help/wireguard-and-mullvad-vpn to prevent leaks when wireguard is active (note: active)
create script to start wireguard on startup
nano /etc/rc.local
#!/bin/sh -e
/usr/bin/wg-quick up usa
exit 0
Client
- Name: win-client
- IP (interface 1, LAN): 100.10.10.10
- OS: Windows 10
set client IP on LAN Segment (elevated prompt)
netsh interface ipv4 set address name="Ethernet0" source=static addr=100.10.10.10 mask=255.255.255.0
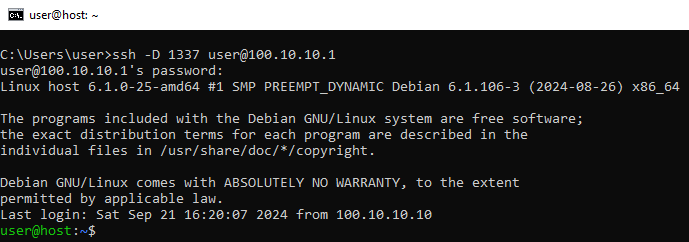
connect to “router” and create SOCKS proxy
ssh -D 1337 [email protected]
Usage
create socks proxy by connecting to “router” VM using ssh.
set proxy on firefox or any other program that support socks proxies.
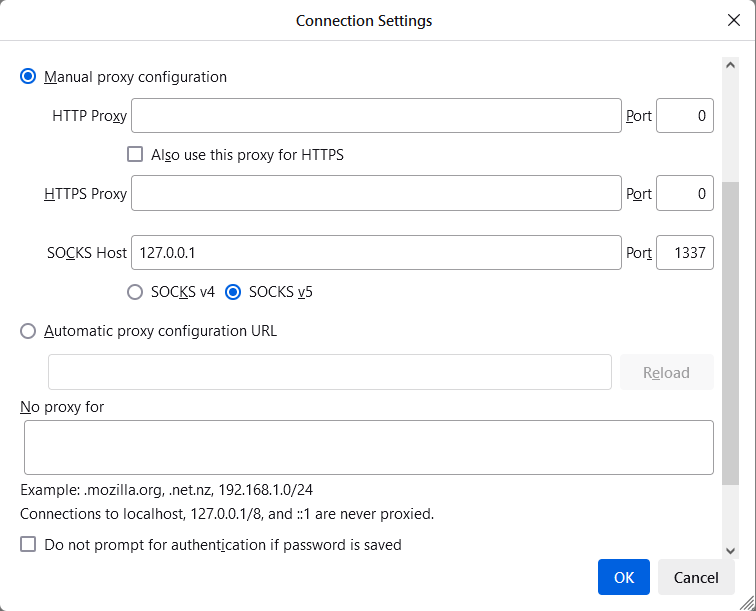
profit!